The CMMC Tsunami: How Ripples Became Waves—and Now a Storm Threatens the Defense Industrial Base

Far offshore, deep under the ocean, a powerful shift occurs—an earthquake, a volcanic eruption, or a landslide.
At first, the surface looks almost calm.
There’s no immediate towering wall of water.
Just a subtle change: a slight pull of the tide, a few ripples moving outward.
But beneath the surface, an unstoppable force has been unleashed.
A massive surge of energy races silently across the water at hundreds of miles per hour. As it approaches land, the seafloor rises. The wave, once almost invisible, grows into a towering wall of water.
When a tsunami hits, it doesn’t just flood the coastline—it redraws it.
Entire towns are swept away.
Harbors are wiped clean.
The landscape is forever altered, and only the most prepared—or the highest ground—survives intact.
Tsunamis are not ordinary storms.
They are transformational forces.
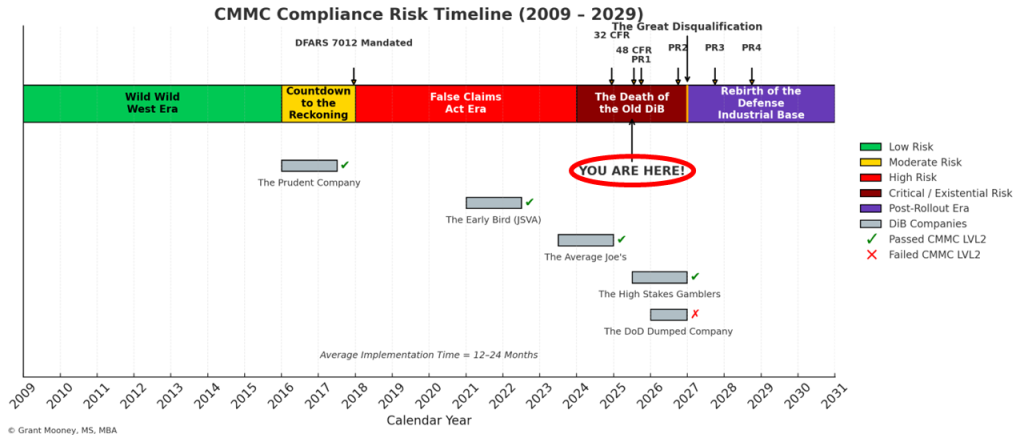
Now, across the Defense Industrial Base (DIB), another tsunami is approaching—not made of water, but of regulation, enforcement, and cybersecurity evolution.
This tsunami is called CMMC (Cybersecurity Maturity Model Certification).
The warning signs have been there. The ripples started years ago.
The only question left is: Will you be ready when it hits?
🌱 The First Ripples: Early Warnings Ignored
Years ago, the Department of Defense (DoD) recognized a growing threat: foreign adversaries were targeting the U.S. through the supply chain. Sensitive defense information was bleeding out through small and mid-sized contractors who lacked robust cybersecurity.
In response, early guidance like NIST SP 800-171 and DFARS 7008 & 7012 requirements were issued. These policies were the first ripples—small movements in the water that signaled a shift in expectations. While many companies unknowingly drifted closer to this impending disaster, each DFARS 7008 and 7012 clause they signed legally obligated them to have already fully implemented NIST 800-171 standards. These contractual commitments weren’t mere bureaucratic formalities—they were early tremors, subtle but undeniable confirmations of the seismic event beneath the surface. Those early ripples, largely ignored or misunderstood, were legal liabilities accumulating beneath calm waters, now coalescing into the regulatory tsunami known as CMMC.
But many companies treated these requirements as minor disturbances. Some completed a checklist. Some promised improvements without making real changes, some attested to NIST 800-171 compliance without knowing a thing about it. And others simply ignored the warnings altogether, anchored by the belief that bigger threats only happen to bigger ships.
The ripples were there. But few adjusted their course.
🌊 The Rising Waves: CMMC Begins to Form
As data breaches multiplied and cyberattacks grew more sophisticated, the ripples grew into undeniable waves.
The Department of Defense realized more dramatic action was needed to protect national security.
Thus, the Cybersecurity Maturity Model Certification (CMMC) was born.
No longer would companies self-attest to their cybersecurity practices.
Third-party assessments would now be required to prove compliance.
Without certification, companies would be barred from executing on defense contracts.
The water was no longer gently stirring. It was rising.
And those waves carried with them a heavy message: Adapt or be cast adrift.
💥 The Earthquake Beneath: A Tectonic Shift in the DIB
Many companies didn’t notice it—but while they worked through proposals and deliveries, a massive earthquake rumbled far beneath the surface.
- Threat actors were becoming state-sponsored and far more sophisticated.
- Legislative pressure was mounting on the DoD to shore up its vulnerabilities.
- Public trust in the resilience of the U.S. defense supply chain was beginning to erode.
This earthquake is what triggered the tsunami—the seismic force of CMMC requirements reshaping the entire defense contracting landscape.
By the time the first wall of water appears on the horizon, it’s already too late for last-minute scrambling. The energy unleashed cannot be stopped—it can only be anticipated and prepared for.
🌊🌊🌊 The Tsunami Approaches: What Happens Next?
The full enforcement of CMMC is not a distant possibility—it is an inevitable, crashing wave speeding toward the DIB.
Companies that fail to adapt will face existential consequences:
- Loss of Contracting Opportunities: Without certification, companies will be disqualified from defense projects.
- Reputational Damage: A company caught unprepared signals unreliability not just to the DoD, but to prime contractors and teammates.
- ⚖️ Whistleblowers, False Claims Act, and Cybersecurity Noncompliance
- “False cybersecurity certifications are no longer a hidden risk. They are ticking time bombs.” – U.S. Department of Justice
- Under the False Claims Act (FCA), companies that submit false information to the government—or falsely certify compliance with federal regulations—can be sued for massive damages.
And cybersecurity compliance is now a major target. - In fact, the Department of Justice launched the Civil Cyber-Fraud Initiative in 2021, focusing specifically on holding contractors accountable when they:
- Knowingly misrepresent their cybersecurity practices,
- Fail to report breaches,
- Or falsely claim they meet contract requirements like DFARS or CMMC preconditions.
- 🔹 Example: In 2022, Aerojet Rocketdyne settled for $9 million after a whistleblower (their former cybersecurity executive) alleged that the company failed to comply with DFARS cybersecurity clauses—even though they were required to under federal contract terms (DOJ announcement).
- 🔹 Key point: Individual employees—not just agencies—can trigger these lawsuits.
Under the FCA’s qui tam provisions, whistleblowers are entitled to a portion of any recovered settlement. - In the context of CMMC, if a company falsely claims readiness or compliance to win a defense contract, they could face millions of dollars in penalties—and public reputation damage that is even harder to repair.
- Financial Loss: Losing access to defense contracts could cripple companies, especially small and mid-sized firms that depend on this business.
This isn’t just a compliance checkbox. It’s an industry-wide rearrangement—a reshaping of who stays and who goes.
The coastline will be forever altered.
🛡️ Preparing for the Tsunami: Riding the Wave, Not Fighting It
The good news?
You can survive.
You can thrive.
But only if you start moving now.
Preparation looks like:
- Understanding your CUI
- Understanding your current cybersecurity posture
- Developing robust System Security Plans (SSPs) and Plans of Action and Milestones (POA&Ms).
- Engaging early with experts who can guide your certification journey.
- Building a cybersecurity-first culture within your organization—before it’s forced upon you.
The organizations that prepare now will not only survive the tsunami—they’ll be the new leaders in the reshaped Defense Industrial Base.
Those who treat CMMC as an opportunity, not a burden, will rise with the wave.